Here’s a look at the most interesting products from the past month, featuring releases from Action1, AwareGO, BlackBerry, Box, Castellan Solutions, Cloudflare, Code42, Cossack Labs, F5 Networks, Immuta, IriusRisk, MetricStream, MobileSphere, Nerdio, NetQuest, Oxeye, Ping Identity, Pondurance, SentinelOne, Syxsense, Tenable, ThreatConnect, Tufin, Veriff, Verimatrix, and Zerto.


Open source cloud native security analyzer Terrascan embeds security into native DevOps tooling
Tenable enhanced Terrascan, an open source cloud native security analyzer that helps developers secure Infrastructure as Code (IaC). The new capabilities enable organizations to embed security into their DevOps tooling, pipelines and supply chains, mitigating risks before infrastructure is provisioned.


IriusRisk V4 enables teams to present progress of threat modeling to senior leadership
The new version of the platform is designed to make it easier for teams to generate threat models of systems, share them collaboratively across their organization, and demonstrate the impact of improved software security to executives within the business.


Castellan releases Crisis Management module to drive organizational readiness and response
Castellan’s SaaS platform offers a fully integrated solution that helps users analyze and prioritize risk, develop actionable response and recovery plans, communicate with employees via multiple channels, stress test plans via plausible scenarios, and mobilize response teams in the critical moments of an incident occurring – all within a single platform.


Zerto In-Cloud for AWS protects mission-critical applications running on Amazon EC2
Zerto In-Cloud for AWS improves volume replication efficiency at scale across regions and zones, and optimizes orchestration workflows to achieve minimal data loss and rapid recovery to achieve your Recovery Point Objective (RPO) and Recovery Time Objective (RTO). Zerto In-Cloud for AWS brings a cloud-native DR to AWS workloads that are born in the cloud or migrated into the cloud.


Immuta SaaS enables customers to control their own cloud environment
Immuta’s SaaS deployment is a fully managed cloud service designed to improve data security by enabling data teams to register data from one or multiple cloud data platforms and be completely operational within minutes.


Verimatrix Streamkeeper empowers media and entertainment industry to combat piracy threats
Streamkeeper empowers customers to hunt down and take out OTT pirates who steal content such as live sports and premium movie as they are distributed from the source to the endpoint (mobile app/user level).


ThreatConnect 6.4 allows security operations and CTI analysts to improve threat intelligence process
ThreatConnect combines its Threat Intelligence Platform (TIP) and Security Orchestration and Automation platform (SOAR), creating a continuous feedback loop that helps make Intelligence-Driven Operations a reality. This latest product release builds upon the foundation of Intelligence-Driven Operations, empowering the workflow of threat intelligence and security operations teams individually and together.


Acra: Open-source database protection with field-level encryption and intrusion detection
Acra’s features enable the implementation of application-level encryption in modern cloud applications, saving development costs and allowing tighter grip on sensitive data lifecycle.


SentinelOne Singularity Mobile combats mobile malware and phishing attacks
With Singularity Mobile, powered by Zimperium, the Singularity XDR platform now expands to deliver Mobile Threat Defense coverage to iOS, Android, and ChromeOS that is on-device, adaptive, and real-time, to thwart mobile malware and phishing attacks without cloud connection dependency.


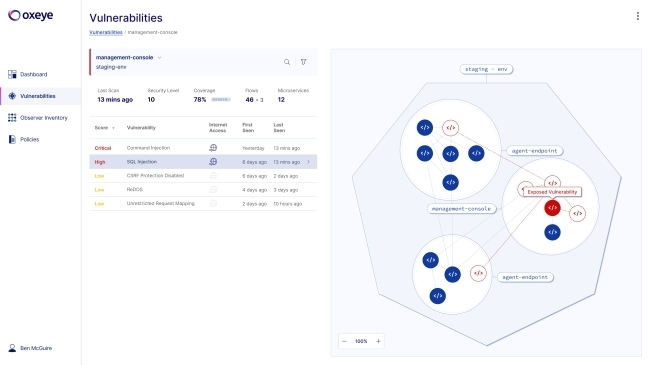
Oxeye CNAST platform delivers contextualized risk assessment for cloud native applications
The new platform identifies code vulnerabilities, open-source vulnerabilities, and secrets to highlight the most critical issues in the software development lifecycle.

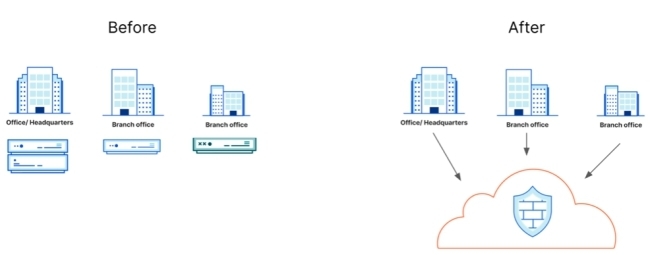
Cloudflare expands firewall capabilities to help companies secure their entire corporate network
With Cloudflare’s new cloud firewall functionality, CIOs can better secure their entire corporate network, apply zero trust policies to all traffic, and gain deeper network visibility. And since Cloudflare’s firewall runs everywhere, CIOs no longer need to rely on centralizing traffic on one box in one location, physical or virtual.

F5 unveils multiple security offerings to prevent automated and human-driven malicious activity
F5’s complementary solutions now offer comprehensive account takeover protection on a single platform. Organizations can better defend against bots targeting their web properties and those of third-party providers with Aggregator Management, recognize legitimate users throughout the customer journey with Authentication Intelligence, and gain insight into client-side digital skimming attacks with Client-Side Defense.


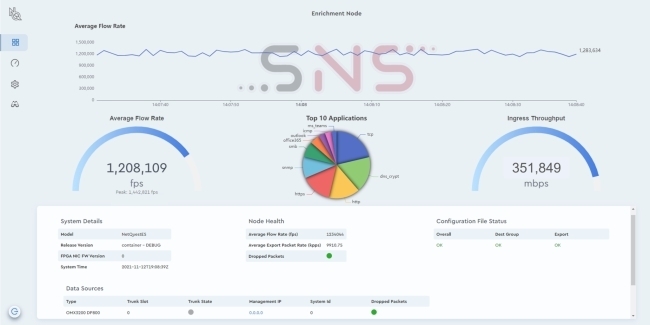
NetQuest Streaming Network Sensors extend visibility and optimize threat detection
The Streaming Network Sensors feature NetQuest’s unsampled flow metering performance capable of scaling flow metadata generation from a single 10G link to multiple 100G network links in a compact 1RU footprint. Flow data at this scale makes the sensors ideal for securing large-scale regional networks, data center backbones, ISP peering and international optical links.

Action1 RMM platform updates empower IT teams to secure their remote and hybrid workforce
Action1 Corporation released the new version of its RMM platform, giving MSPs and IT departments real-time visibility and control over corporate endpoints and empowering companies to support hybrid workforce.


Tenable.cs prevents cloud security risk and improves developer productivity
With the release of Tenable.cs, Tenable will help organizations protect the full cloud-native stack throughout the DevOps lifecycle, from the time applications and infrastructure are defined in code through production usage.


Code42 adds new insider threat detectors for government security teams
The new data exfiltration detectors give security teams full visibility when files are shared, downloaded, or emailed to untrusted destinations on OneDrive, Google Drive, Box, Office 365 and Gmail, whether those insider risk events take place on a computer, in the cloud or over email.


AwareGO Human Risk Assessment for Enterprise measures employees’ cybersecurity behavior
Based on human-behavioral science, the cloud-based solution allows companies to measure employees’ knowledge and behavior across several recognized threat vectors, such as phishing, remote work, passwords, and more, ultimately quantifying the company’s cyber resilience.


Nerdio adds backup and disaster recovery features to improve Azure Virtual Desktop resiliency
Nerdio Manager extends the native AVD service rather than replacing it like other proprietary VDI management solutions on the market. Through separate products tailored to meeting the needs of MSPs and enterprises, it delivers over 200 features that the native service lacks to simplify management, ensure efficient operations through automation, and lower compute and storage costs.


Syxsense Secure protects businesses against the Log4j vulnerability
Syxsense announced the ability to scan for Log4j using Syxsense Secure, identifying endpoints that are exposed to this new vulnerability.


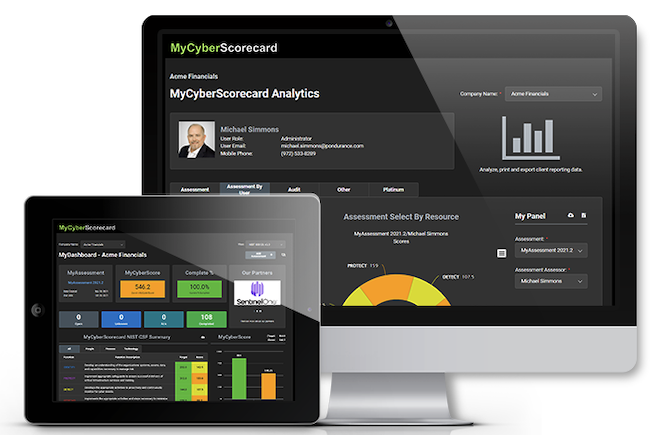
Pondurance Cyber Risk Assessments analyze and visualize potential cybersecurity gaps
Pondurance Cyber Risk Assessments powered by MyCyberScorecard deliver streamlined and efficient cybersecurity assessment processes aligned with regulatory standards and compliance requirements, allowing organizations to gain greater trust with customers, partners, regulators and insurance providers.

PingOne Authorize delivers enhanced authorization capabilities for enterprises
PingOne Authorize gives organizations centralized, fine-grained control over who has access to data, services, and APIs. Organizations can restrict access based on customer consent, real-time risk signals, or entitlements and contextual information, regardless of where that contextual data is stored.


Tufin Security Policy Builder App automates corporate security access policies
Integrating with Tufin’s SecureTrack, the Security Policy Builder App automates the design of network and cloud security access policies based on existing access and aligned to compliance models. In addition, the app operationalizes security policies to identify the exposed attack surface for prioritized response based on a company’s unique definition of risk to the business, and empowers the user to take effective mitigation steps or tracking for compliance assurance.


MobileSphere SLYGuard secures communications on popular messaging applications
SLYGuard provides an encryption tool to encrypt and decrypt text and images sent using any messaging app without the threat of the content being exposed or intercepted. Text and image encryption/decryption hides the content before sending it to the intended person.


MetricStream’s software release measures cyber risk in monetary terms
MetricStream announced new native capabilities for Advanced Cyber Risk Quantification and Simulation to measure cyber risk in monetary terms, along with intuitive risk assessments, expanded compliance risk management capabilities, and enhanced visibility into third and fourth-party risks.


Veriff’s metaverse identity verification solution protects users from fake accounts and bots
Following the age appropriate design code, Veriff’s technology helps to verify the identities of metaverse users while also protecting underage users, especially young children, from inappropriate or age restricted content or from people pretending to be someone else online.


BlackBerry Guard XDR protects enterprises and governments against evolving cyber threats
The BlackBerry Guard managed XDR solution provides coverage beyond endpoints by seamlessly integrating Cylance AI-powered BlackBerry Optics, BlackBerry Persona, BlackBerry Gateway, and BlackBerry Protect solutions with Exabeam Fusion SIEM and XDR solutions.


Box launches enhanced tools to drive insights and mitigate security risks
Box announced new monitoring and reporting tools for its Box Admin Console to help customers keep their businesses running securely. These new capabilities include advanced reporting in Box Sign and Box Shield, automated verification controls, and an event stream that provides near real-time visibility into activity across Box.


from Help Net Security https://ift.tt/32XMt64
0 comments:
Post a Comment