Microsoft Exchange servers are an ideal target for attackers looking to burrow into enterprise networks, says Microsoft, as “they provide a unique environment that could allow attackers to perform various tasks using the same built-in tools or scripts that admins use for maintenance.”
And while they are not the initial entrance point in the majority of cases, the company has witnessed lately a rise in attacks aimed at compromising Exchange servers by exploiting an unpatched flaw – more specifically CVE-2020-0688, a patch for which was released in February 2020.
While the attackers need to have compromised, valid email credentials to access the server before attempting to exploit the flaw, they are obviously succeeding in getting their hands on them. (Kevin Beaumont explained why that’s not much of a problem.)
“This is an attacker’s dream: directly landing on a server and, if the server has misconfigured access levels, gain system privileges,” the Microsoft Defender ATP Research Team noted. And, unfortunately, there are still too many internet-facing, unpatched Exchange servers out there.
The attack chain
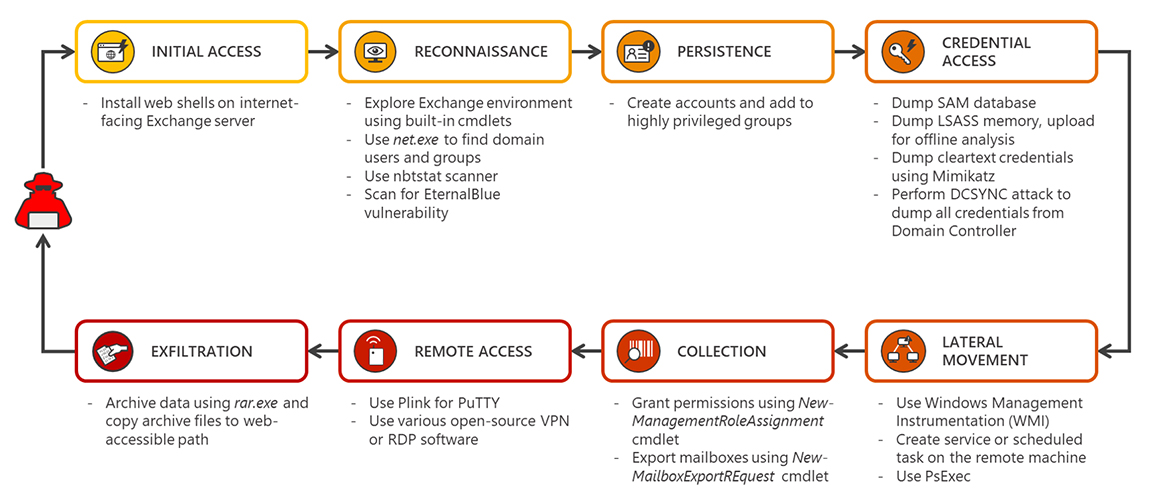
According to Microsoft, April was the month when multiple campaigns began to target Exchange servers.
After gaining access, the attackers proceeded to install web shells to allow them to control the server remotely, and then started exploring its environment for info on domain users and groups, other Exchange servers in the network, and mailboxes, as well as scanning for vulnerable machines on the network.
They achieved persistence on the compromised Exchange server by adding new user accounts and elevating their privileges, then proceeded extract credentials from the Security Account Manager (SAM) database, the Local Security Authority Subsystem Service (LSASS) memory, and the Domain Controler.
They used WMI (Windows Management Instrumentation) and PsExec (a Microsoft tool for running processes remotely) to achieve lateral movement, exported mailboxes via Exchange Management Shell commands, created a network architecture that would allow them to bypass network restrictions and remotely access machines through Remote Desktop Protocol (RDP) and, finally, they compressed the data and put it in a web-accessible path for easy pickup.
Mitigation and prevention
“As these attacks show, Exchange servers are high-value targets. These attacks also tend to be advanced threats with highly evasive, fileless techniques,” the team noted.
The attackers are also trying to disable security tools like Microsoft Defender Antivirus, archive scanning and automatic updates to increase their stealth.
Aside from doing the best possible thing – implement the latest security updates as soon as they become available – admins are advised to:
- Audit MS Exchange servers regularly for vulnerabilities, misconfigurations, and suspicious activity
- Regularly review highly privileged groups and the list of users in sensitive roles for anomaliers (e.g., suspicious additions)
- Practice the principle of least-privilege, maintain credential hygiene, and enable multi-factor authentication.
Microsoft naturally also touts its Microsoft Defender Advanced Threat Protection security platform as a means to add protection to Exchange servers, automatically block behaviors like credential theft and suspicious use of PsExec and WMI, prevent attackers from tampering with security services, and to prioritize alerts so that attacks are spotted before they can do much damage.
from Help Net Security https://ift.tt/3eAGjdd
0 comments:
Post a Comment