Despite what you might have heard, there’s no shortage of people looking for jobs in cybersecurity. Every open position triggers stacks of resumes, but the challenge is finding the right people with the right skills to do the job.

Most resumes include impressive lists of certifications and degrees, but that’s not what employers are looking for the most. If you’re seeking a job in cybersecurity, the best way to set yourself apart is to demonstrate an aptitude for the skills actually needed to be a great threat hunter, investigator or researcher. But how can you demonstrate that aptitude if you don’t already have a job doing it?
It’s pretty simple, actually. Just find recent threats that have not yet been analyzed and write an analysis about them.
That’s not as complicated as it may sound. You can actually just search the web for new and relatively unknown malware. There are so many different ways to do this.
As a simple illustration, if you want to examine some opportunistic attackers, one useful technique is to search for a hot topic (especially one that is emotionally charged) and add phrases like “free download” to the search. For example, in a recent search for “stop the steal” (a powerful catch phrase for a segment of the U.S. population) and “free download,” one of the top results pointed to an algorithmically generated (DGA-looking) domain with an article about U.S. presidential impeachment. Clicking on the result redirects to a page that uses a fake landing page with a “human varication” check (complete with false Captcha logo) designed to trick users into allowing the domain to push notifications to the desktop.
Here’s how it looks:

After being redirected to a couple pages using trickery to enable notifications on the user’s desktop, those notifications led to other pages directing users to download Chrome extensions that share many characteristics with other known-malicious extensions.
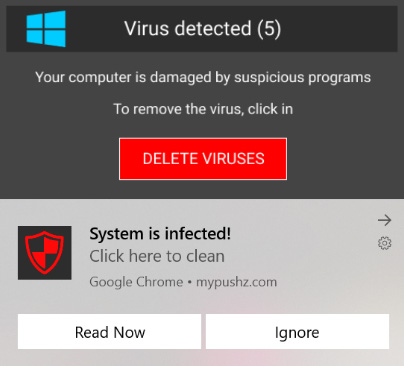
These notifications are delivered to the desktop even without the browser. The screenshot above shows one of the notifications: a fake virus alert designed to trick users into downloading nefarious “security software.” How do I know it’s fake? There is no anti-virus software installed on my research laptop.
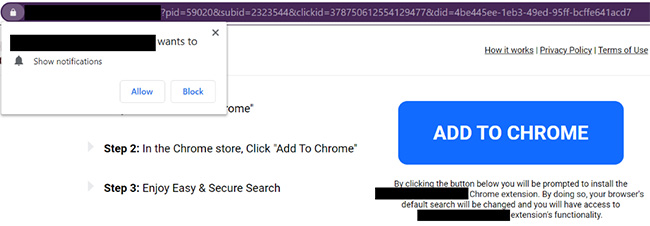
Below, you can see a page loaded by one of the notifications. It directs the user to install a low-reputation browser extension with similar characteristics to other known-malicious extensions and access to every website you visit and everything you type on those websites.
After only about 15 minutes on this trail, here’s one of the most stunning things I found:
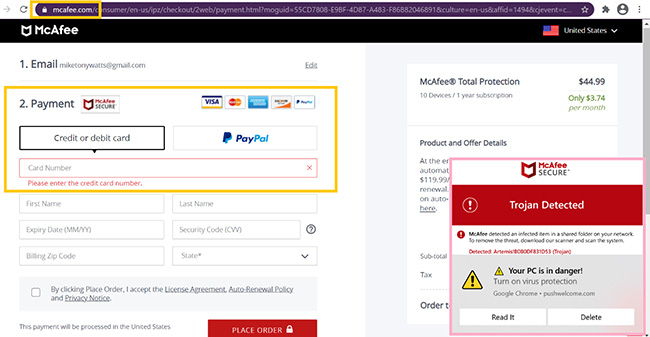
The pink box drawn over the above screenshot shows a fake notification telling me McAfee detected a trojan on the system. This is impossible because, again, McAfee is not installed on this clean test system. You can also see the notification was sent from the domain in the first screenshot – the redirect encountered from a domain that seemed to be using blackhat SEO to target Trump supporters.
However, this is where it gets really interesting. I was ultimately redirected to the REAL McAfee website to purchase an antivirus license, as shown in the yellow boxes (mcafee.com is shown to be the actual server that has passed all the browser security checks).
Consider this a pointer to your first security research project. Could blackhat affiliates be profiting by linking to the McAfee website? Or are they convincing people they need to buy McAfee, leading them to the real McAfee page and then siphoning credit card information using malicious browser extension they installed?
The example above might be a bit of a detour from the topic at hand – proving your passion for cybersecurity – but it shows how a simple web search can surface threads to investigate, which could certainly lead to sensational news depending on what you find.
When applying for a cybersecurity job, being able to reference research that has landed you in the headlines for objectively positive reasons can be far more powerful than a resume bullet point saying you do research. But the bigger point here is that finding examples like this did not require any sophistication beyond doing 15 minutes of creative searching from my research laptop while sitting in bed (literally). I promise, you can do the same whether you are an infosec veteran or have never formally worked in the industry.
Taking your research a step further
While performing “hot topic” searches like that can be a fun and interesting exercise, another technique is using search to find recent threats. The threats being “recent” means the likelihood of them being analyzed and documented already is probably low, meaning you should have the opportunity to document novel intelligence for the industry – discovered by you.
For these searches, try using “Past Week” or “Past Month” search modifiers while filtering for keywords on security-focused sites. For example, consider the following:
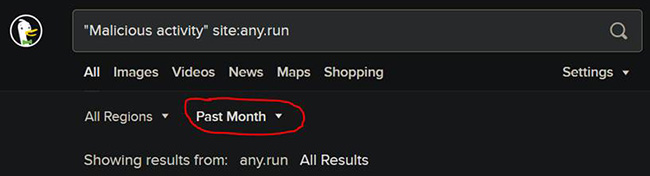
The screenshot above shows a search for the phrase “malicious activity” within the popular malware testing sandbox any.run with results limited to pages from the past month. One of the top results is this file that uses PowerShell to drop code that ultimately connects to saico015.linkpc[.]net (168.119.170[.]202) on port 6666. That is probably interesting. The sandbox replay is here.
There are very few other files in VirusTotal that also communicate with the same domain. All were found within the past couple of weeks (of this writing), and all look quite bad. They also seem to share the same characteristics as the any.run result, so there is a good chance these are all related.
Searching for the command and control (C2) domain returns extremely few results. Another top result points to an executable that uses the exact same C2 server identified previously, plus another domain. Searching for both domains also returns an extremely small number of results, none of which have already been written about by other threat researchers. This means the activity could possibly be considered a “campaign,” that is, use of malware in a customized and identifiable way. This find could be a good candidate to explore and document in a threat report.
As someone who has hired my fair share of security analysts as well as worked as one, my point is simply that if you are trying to decide between spending a weekend binge watching Expanse on Netflix or doing some searches that could lead you to writing a novel threat report on a previously undocumented hacking campaign, the later will get you into the industry faster. (Although, admittedly, that is a tough choice!)
A bonus in the example above is that the malware has been identified in the links above as AsyncRAT. This is great because that malware is written in .NET, which is extremely easy to decompile with tools like DotPeek. Without being a programmer, it is likely you can open a .NET executable in a decompiler and find interesting stuff just by browsing how the executable was written. (For a broad introduction to binary analysis and tools that will tell you if an executable is .NET or otherwise, Tstillz has a number of interesting posts, including this one. Or just try doing a search for “static malware analysis” to get started.)
For example, opening one of the in-the-wild malware executables from the links above in a decompiler exposes a “Settings” class (pictured below) that could provide more clues to follow in an analysis and investigation of this campaign. The screenshot below shows the results of decompiling the Settings class. (I did nothing to find this other than open the file in DotPeek and click on “Settings” in the left-side Assembly Explorer.)

This screenshot shows the encoded settings, as well as the decode functions shown just below them. From here it is simple to follow those function calls to see how to decode those strings.
Again, this example was found without access to any special equipment or networks. You can do the same searches, or better yet, you can creatively find your own enhanced searches that will give you access to a stream of threats that need to be turned into threat intelligence through your writing, videos, and presentations!
Bottom line: You don’t need a job as a threat researcher/investigator to establish yourself as a proven threat researcher/investigator. And in the eyes of a prospective employer, this is worth much more than any degree or certification.
That said, what strategy can you use to ensure your research/writing/videos/presentations are useful and reliable? That’s what my next Help Net Security article will cover.
from Help Net Security https://ift.tt/3dGVSC0
0 comments:
Post a Comment