The Mitre Corporation has released the ninth version of its ATT&CK knowledge base of adversary tactics and techniques, which now also includes a newly created ATT&CK matrix for containers.
Source: MITRE
MITRE ATT&CK v9
ATT&CK covers a number of matrices:
- For Enterprise (preparatory, Windows, macOS, Linux, cloud, and network-based techniques, and now also container-based ones)
- For Mobile (covering the Android and iOS platforms)
- For ICS
The ninth version of the knowledge base includes 16 new Groups, 67 new pieces of Software, and updates to 36 Groups and 51 Software entries (more info about specific additions can be found here.)
MITRE has also revamped data sources, consolidated IaaS platforms, added a Google Workspace matrix, updated macOS-based attack techniques and added macOS-specific malware, and has created a brand new ATT&CK for Containers matrix.
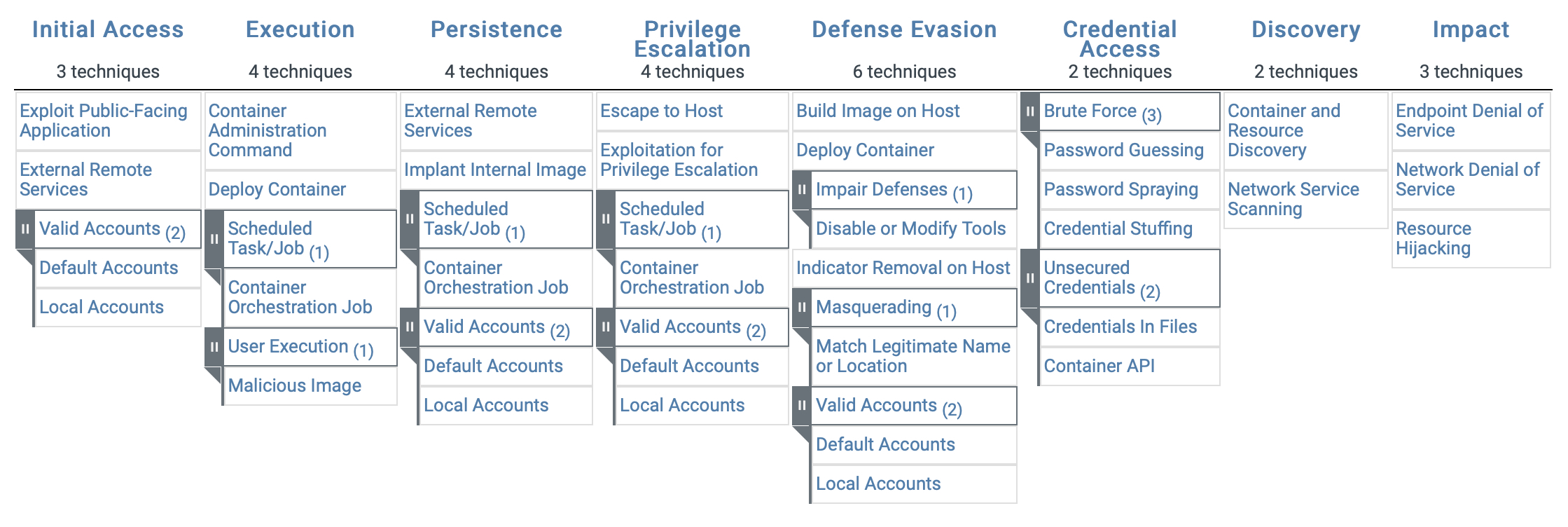
ATT&CK for Containers
ATT&CK for Containers covers both orchestration-level (e.g., Kubernetes) and container-level (e.g., Docker) adversary behaviors. It also includes a set of malware related to containers.
“The ATT&CK for Containers builds on efforts including the threat matrix for Kubernetes developed by the Azure Security Center team for Azure Defender for Kubernetes. The Center for Threat-Informed Defense expanded on this initial framework by documenting real-world attacks, with Microsoft and other partners providing guidance and feedback throughout the process,” Microsoft noted.
“Building the ATT&CK for Containers matrix is helpful in understanding the risks associated with containers, including misconfigurations that are often the initial vector for attacks, as well as the specific implementation of attack techniques in the wild. This knowledge informs approaches for detecting threats, and thus helps in providing comprehensive protections, as more and more organizations adopt containers and container orchestration technologies like Kubernetes.”
While working on this new matrix, MITRE engineers learned from community feedback that the vast majority of container-based attack activity they’ve observed leads to cryptomining.
“However, evidence from a number of parties led us to conclude that adversaries utilizing containers for more ‘traditional’ purposes, such as exfiltration and collection of sensitive data, is publicly under reported. Ultimately, this led the ATT&CK team to make the decision to include container-related techniques in ATT&CK,” said Jen Burns, Lead Cybersecurity Engineer, ATT&CK Team Member and Cloud Lead at MITRE.
The next update of the ATT&CK knowledge base is scheduled for October 2021, and will include updates for the ICS and Mobile matrices, as well as better coverage of macOS and Linux techniques.
from Help Net Security https://ift.tt/3tezyEy
0 comments:
Post a Comment