Less than half of organizations have a privileged access management strategy in place for digital transformation technologies, like RPA, according to a CyberArk report.

The report provides practical recommendations from information security executives based on their first-hand experiences. They share key recommendations for how organizations can securely adopt RPA while mitigating potential risks, including:
- Limiting access for reprogramming robots – Reduce the risk that comes with RPA permissions – like the ability to reprogram robots – by securely managing credentials to RPA tools and training RPA teams on secure software development practices.
- Automating credential management – Successful RPA deployments require automated credential management, including machine-generated passwords, automatic password rotation, identity verifications and just-in-time or time-limited credential access.
- Establishing robust processes for monitoring RPA activity – Rapidly detect and respond to unauthorized or anomalous robot behavior by assigning human managers, enforcing least privilege and making actions traceable.
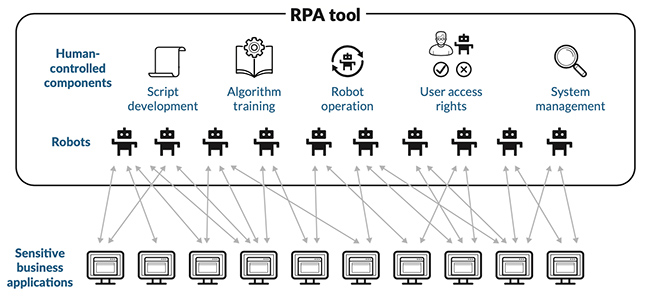
Conceptual overview of an RPA tool
“From finance and HR to manufacturing, organizations are rapidly adopting RPA to drive new efficiencies for their business and deliver innovative services to customers,” said Marianne Budnik, CMO, CyberArk.
from Help Net Security https://ift.tt/39ZxU0c
0 comments:
Post a Comment