A phishing campaign aimed at harvesting Office 365 account credentials is employing a variety of tricks to fool both email security sistems and recipients: the phishing emails come from a compromised enterprise account, through the secure email system Zix, to make recipients believe that the offered link isn’t malicious.
The phishing email
The phishing emails are sent from a compromised email account belonging to a real estate services provider (Authentic Title, LLC), and ostensibly contain a closing settlement counter offer. To view it, the recipients are asked to follow a link included in the email.
As the emails are sent via Zix, they sport a header and a footer proclaiming that “This message was sent securely using Zix” and “This message was secured by Zix” – which might be enough for some users to decide the email is legitimate and they can safely follow the provided link.
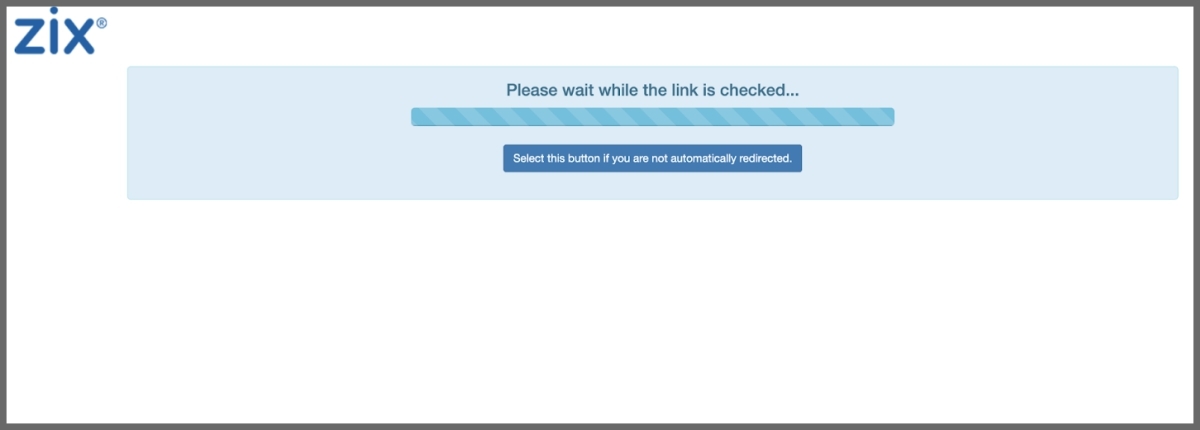
“[The] link takes the message recipient to an official Zix authentication site (zixcentral.com) that checks the link for safety. After checking the link, the Zix page takes the recipient to a Microsoft OneNote page,” Abnormal Security researchers explained.
Unfortunately, the link on that page is malicious, and clicking on it will trigger a request to share Office 365 or other email account credentials:

Tricks of the trade
“This attack uses a fairly common technique to evade email security, but with a twist. Many attacks use a similar strategy as this attack and hide behind multiple layers of redirect links in order to confuse security systems,” the researchers noted.
“This attack took that strategy a step further by using a Zix link in order to take advantage of the trust placed in Zix and other secure messaging systems. Because the first page after the Zix link was a seemingly benign page hosted by Microsoft, Zix was unable to immediately tell that the link was malicious.”
Hosting malicious content on a Microsoft service is also a trick often used by cyber crooks to bypass security protections (that inherently trust those sources) as well as to “legitimize” malicious messages in the eyes of the recipients.
from Help Net Security https://ift.tt/3y7Zs06
0 comments:
Post a Comment