The vast majority of ransomware attacks now include the theft of corporate data, Coveware says, but victims of data exfiltration extortion have very little to gain by paying a cyber criminal.
The stolen data has likely been held by multiple parties and not secured, and victimized organizations can’t be sure that it has been destroyed and not traded, sold, misplaced, or held for a future extortion attempt, they explained.
Also, the data may be published before a victim can respond to an extortion attempt, and the threat actors may not provide complete records of what was taken even if the victim pays up.
“Despite the increase in demands, and higher prevalence of data theft, we are encouraged that a growing number of victims are not paying,” Coveware noted.
“Over hundreds of cases, we have yet to encounter an example where paying a cyber criminal to suppress stolen data helped the victim mitigate liability or avoid business / brand damage. On the contrary, paying creates a false sense of security, unintended consequences and future liabilities.”
Other Q1 2021 ransomware trends
The incident response firm has compiled a report of ransomware incident response trends during Q1 of 2021, and this is what they have found that the average ransom payment has reached $220,298, which is an increase of 43% when compared with that in Q4 2020.
The median ransom payments has also increased in the same period, from $49,450 to $78,398 (i.e., by 58%). Both of these increases have been heavily impacted by the activities of the gang wielding the CloP ransomware, which were very active in Q1 2021, hit a great number of big organizations via vulnerable instances of the Accellion’s FTA solution, and demanded bigger-than-usual sums.
Other trends include:
- Sodinokibi (aka REvil) continued to top the list most common ransomware variants
- Several RaaS operations focusing on developing encryption modules for Unix and Linux
- Small businesses still disproportionately affected by ransomware attacks
- Businesses in the Professional Services industry (more specifically: law firms) have been heavily targeted by ransomware attackers, followed by organizations in the public sector and healthcare
- Ransomware incident duration / average days of downtime has expanded to 23 days
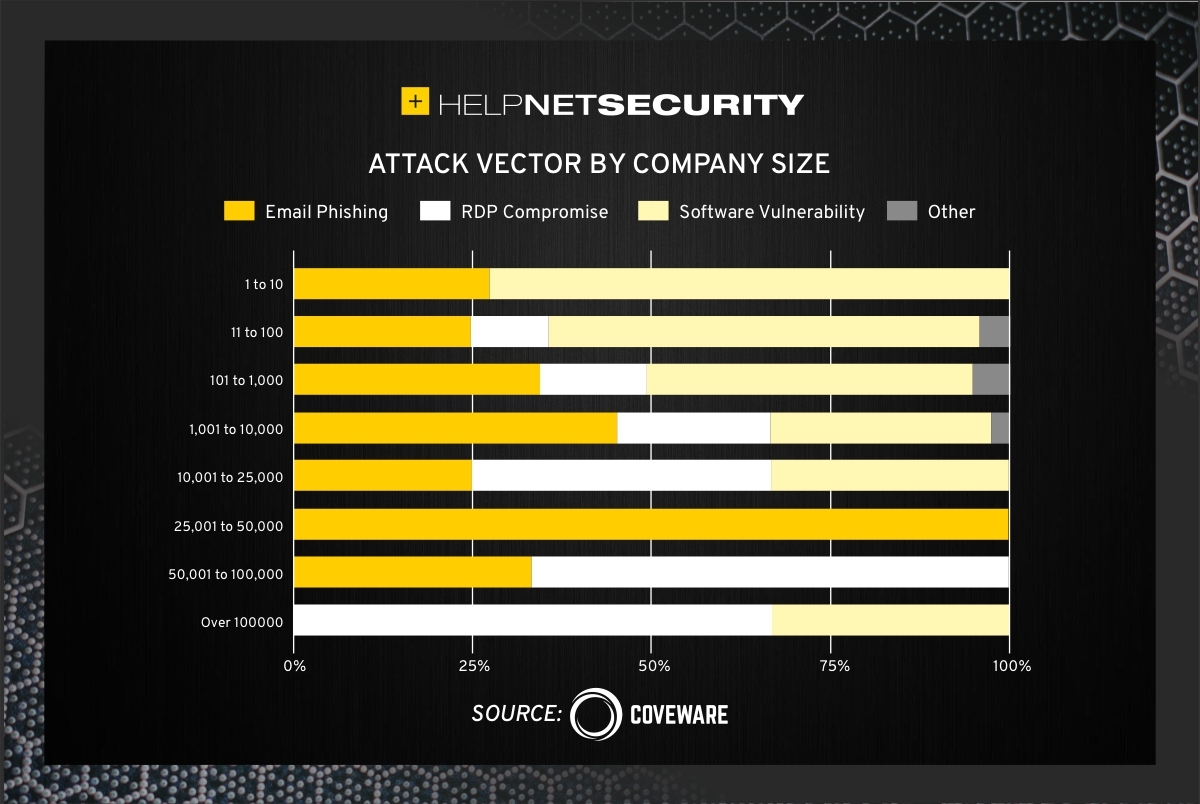
- RDP compromise is, once again, the most common attack vector, followed by email phishing and exploitation of a software vulnerability
“The most common software vulnerabilities exploited during Q1 involved VPN appliances, such at Fortinet and Pulse Secure. Several RaaS services leveraged these VPN vulnerabilities during Q1. Again, it is likely that the actual RaaS operators and affiliates were NOT the party that achieved network access via these vulnerabilities, but rather specialist actors that harvest network credentials and are specifically trained to mass scan for vulnerable IP addresses. These specialists then resell network access to ransomware affiliates who use the access to stage the extortion phase of the attack,” Coveware researchers noted.
“This deliberate division of labor sheds light on how open RaaS operations that focus on smaller victims, like Lockbit, were able to take advantage of vulnerabilities outside of their skillset. Specialization and supply chain coordination also highlights the continued evolution of the cyber extortion economy.”
from Help Net Security https://ift.tt/2R2KKGR
0 comments:
Post a Comment